
The latest news worth knowing and reading

Why rights to control robots are necessary today – and how robotics in the security sector contributes to a sustainable strengthening of stability and security
Those who control robots bear responsibility: Why clear rights are crucial for safety today Robots have undergone remarkable changes in recent years. What was once considered a vision of the future is now an integral part of modern security, inspection and maintenance...

Security Robotics in the final of the GIT SECURITY AWARD 2026
Security Robotics is for the GIT SECURITY AWARD 2026 and has made it to the final thanks to its innovative technologies and solutions.The GIT SECURITY AWARD is an important indicator of developments in the security sector. It reflects the current market dynamics and...

Project launch with Securitas and Security Robotics
Autonomous robots: Versatile applications The wide range of applications for autonomous robots is as impressive as their versatility. These sophisticated technologies are used in a wide range of applications, from logistics centers, where they optimize the movement of...

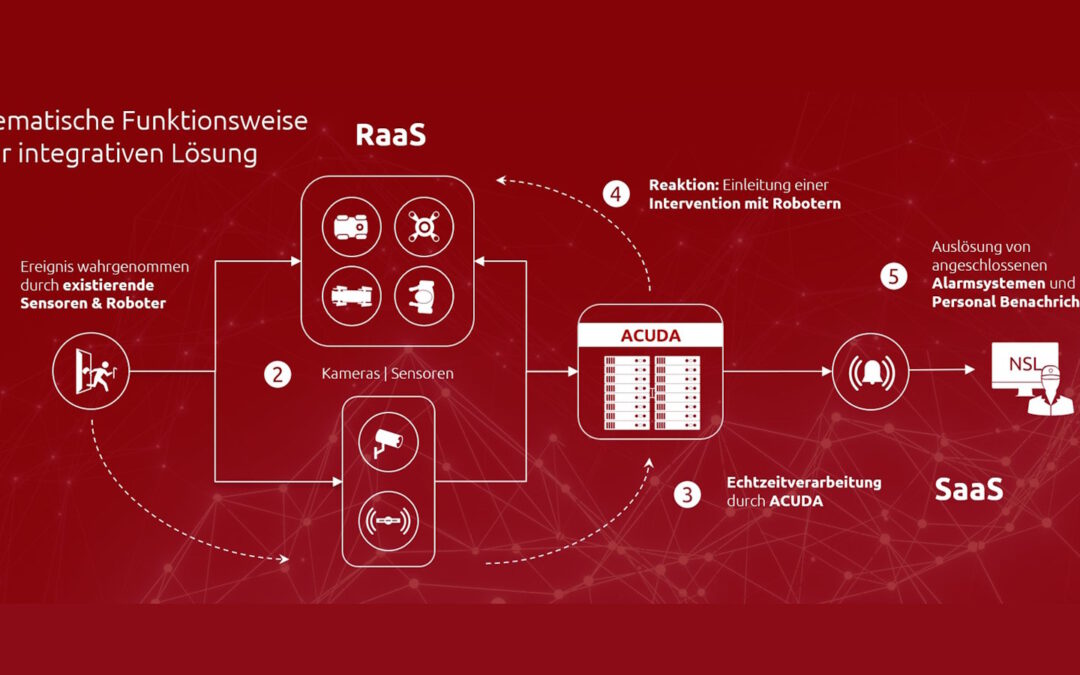
ACUDA – Autonomous Center of Unified Digital Actors (β)
Technical progress and digitalization are playing an ever greater role. Autonomous helpers are becoming increasingly interesting for many companies. They take on monotonous, repetitive or even dangerous tasks and deliver precise and high-quality results. What comes to...

Ambos Security and Security Robotics enter into partnership
- We are stronger together - We are delighted to announce our partnership with Ambos Security from Dresden. The Saxon company has great expertise in consulting and concept development of particularly innovative security solutions, which in future will also include...

Smart Technology + Robotic + AI Solutions – Review of Security Essen 2024
Security Essen: The Global Highlight of 2024 Security Messe Essen, the global hub of the security industry, highlighted its importance as a platform for innovation and expertise exchange in 2024. Celebrating its 50th anniversary, the event attracted more than 500...

Security Robotics Innovation Days 2024
Security Robotics Innovation Days 2024: Innovations and developments The Security Robotics Innovation Days 2024 (ID24), which took place in Leipzig from August 13 to 15, presented the latest trends and technologies in security robotics. Under the motto "Adaptability -...

Industry leaders in Germany focus on autonomous systems: robotics on the rise
Digitalisation and automation are advancing inexorably. In Germany, more and more companies are relying on autonomous robot technologies to optimise their processes and meet the requirements of a modern, efficient industry. These technologies are playing an...
Security Robotics Innovation Days 2024 – Experience flexible security robotics live
We are pleased to announce the Innovation Days - Summer 2024, which will take place from 13 to 15 August in Leipzig. This year, our focus is on the flexibility and adaptability of our robotic platforms. Under the motto ‘The right system for every use case’, we will be...

Unitree meets Security Robotics
Open system robotics solutions at Security Robotics We offer tailor-made software solutions and specialize in the integration of robotic systems. We use hardware such as robots, drones, cameras and sensors, which are always the best platforms and devices for...

Spot on for the next step security on DB
Wie Roboter Schienen(verkehr) sicherer machen können. Die Deutsche Bahn und Security Robotics arbeiten gemeinsam am Fortschritt und verschieben dabei die Standards der Sicherheit.

Kopter-Profi and Security Robotics establish security partnership
The close collaboration between Kopter Profi and Security Robotics promises a pioneering integration of drone technology in the security sector. The combination of experience, expertise and innovative solutions positions this cooperation as the key to optimising security measures.

Security Robotics integration in Geutebrück video management solutions
The integration of autonomous robotics and the ACUDA platform into GEUTEBRUCK GmbH's video management solutions represents a significant step forward in the field of physical security through modern video surveillance. At a time when the digitalisation and networking...

SRob with FLUKE SV600: Innovation in monitoring & inspection
The FLUKE SV600 is a permanently installed acoustic camera that can detect, localize and visualize air and gas leaks as well as changes in the sound signature. Originally developed for industrial applications, it is now also finding innovative uses in safety...

The importance of DIN ISO 9001: How Security Robotics combines innovation and quality
Ensuring long-term quality and innovation at Security Robotics The importance of DIN ISO 9001 certification goes far beyond the mere fulfilment of quality standards. This standard is a strategic tool to ensure sustainable excellence and customer satisfaction. As a...

Security event in Hamburg: knowledge exchange & networking
In just a few days, on 22 & 23 February 2024, Hamburg will once again be the meeting place for security experts. The renowned NBS, Northern Business School, is putting together what belongs together and organising a highly interesting security event consisting of...

The next bis thing – AI use in the security sector
Even though robotics is in our name, mobile, autonomous and very versatile assistants, supporters and colleagues are only ever one part, the hardware part, when we talk about innovations and modern solutions for the security industry. The use of AI, which fulfils a...

Security Robotics: A new member of the BDSW – the Federal Association of the Security Industry
In a world where security and technology are increasingly intertwined, Security Robotics' admission to the BDSW (German Security Industry Association) marks a significant milestone. This young company, which specialises in the development and implementation of...

Goodbye 2023 – welcome 2024
Our look back at a turbulent and exciting 2023 At Security Robotics, it is also a cherished tradition to pause in the first few days of a new year and review the past months. We take time to compare our original plans and intentions with actual events, draw...

Analytical intelligence and innovations in security management – the I2SM of the NBS
The development and characterisation of modern, above all forward-looking security concepts are significantly influenced by 2 circumstances. On the one hand, there are security-relevant events and, ideally, specifications derived from them for the implementation of...

Autonomous robotics ensure greater security in the KRITIS sector
Securing critical infrastructures (KRITIS) is an existential task for every civil society if supply bottlenecks, disruptions to public safety and other dramatic consequences are to be prevented. Modern technologies, in particular autonomous robotics and AI-supported...

Digital communication and data streaming
We often provide information about the importance of autonomous robotic systems, AI support, networked safety concepts, integration of IoT-enabled actuators and our digital solutions ACUDA (Autonomous Centre of Unified Digital Actors) and NUCRON (IoT Injector). The...

Smart, sustainable, cost-efficient – the future of security
Key technologies are always characterised by the fact that they are fast-moving, change, develop, spread, can be used in more and more areas, and grow in their possibilities. It is the same with autonomous robotics and networked AI. We are experiencing a continuously...

Be digital, stay human and love robots – Digital X 2023
There is probably no other European event that is as consistently and broadly dedicated to the topic of digitalisation as Deutsche Telekom's aptly named DIGITAL X event. Based in Cologne, the event remains true to its location year after year, but always brings in new...

Security Robotics Innovation Days – impressions of 2023
Information / knowledge / insight can also be obtained virtually in a variety of ways: via podcast, by reading a brochure, visiting a website and informative phone calls / video calls, etc. However, none of this can replace the personal impression and up-close, direct...

Security robotics roadshow – a short review
1 idea, 1 month, 5 events. The Security Robotics Roadshow was a complete success and made the month of June a particularly exciting and varied one for our team. The approach of participating in very different locations / events and thus informing and even inspiring a...

3…2…1…ARGUS ready for patrolling
Die Innovation Days, unser dreitägiges Event, liegen hinter uns. Und während einige Kollegen dessen Bestandteile wie Zelte, Zäune und sonstige Technik zurückbauten, widmeten sich unsere Softwarespezialisten und Integratoren wieder Ihren Aufgaben, luden große Holzboxen...

Security Robotics Innovation Days 2023 – Experience networked security systems live
The Innovation Days - Summer 2023 are all about digital networking of safety technology. We will present the complete range of our proven robotic walking, cycling, flying and communication robots and demonstrate live how they interact with each other and with other...

Advantages of networked security robots
In current, more aptly called conservative security concepts, technical solutions are often still used too selectively, a camera here, a motion detector there, a light barrier there. Although attention is paid to covering critical and access areas as completely as...

“The Assistant” – SPOTlight on the new member of the robotics team
A package of exciting new robotics is a highlight every time. A few days ago, we were delighted to welcome a new AI colleague to the Security Robotics team, a Spot® Enterprise with a back-mounted arm, and are putting its impressive capabilities through their paces....

Why support from robotic security systems will become a necessity in 2023
This is what robotic security systems do for CRITIS protection If one reviews the events of the last few months and at the same time looks at the challenges facing the economy today, it quickly becomes clear that there is no way around the use of innovative robotic...

Innovation that arrives – Security Robotics nominated for the DEKRA Award 2022
"The only true praise is that which someone else gives you." So when your own ideas and innovations are seen and recognised by a professional institution like DEKRA, it's a reason to be proud. We are pleased to have been included in the circle of nominees for our...

What we (must) expect from a future-oriented education system!
If you look at the curricula of today's high school and grammar school students, it is striking that the topics of artificial intelligence, digitalisation and robotics are hardly given any attention. It doesn't matter which federal state is chosen, because despite...

Because it’s your future as well – A plea for robotics and education
Our world is changing. And this does not only refer to the social, political and climatic conditions, no, also technologically everything seems to develop faster and faster. Ideas once dismissed as science fiction have long since become reality, and changes in the...

Security Robotics as an innovation driver at security Essen 2022
As the most important event in the security industry, security Essen is the highlight of every autumn trade fair and in 2022 it once again proved the enormous importance of the multi-day trade event. As an innovation driver in the field of networked robotic systems,...
The security sector is changing – are you ready for your digital future?
Pressure of expectations, cost explosion, shortage of personnel, shortage of skilled workers, all this will have a particular impact on the entire security sector in 2022. Anyone looking for solutions must rethink security and service concepts and understand where...

Digital transformation in the security sector
Our innovative modular platform solutions Learn all about our innovative modular platform solutions, AI-powered robotics, networked IoT security components, machine-to-machine communication, data normalisation, API and #artificialintelligence. Be curious about the...

Simply ingenious, Security Robotics convinces in live test on the MDR campus in Leipzig
Many company homepages are emblazoned with terms such as agile, innovative, flexible, customer-oriented and they refer to presenting THE individual solution as a matter of course & at lightning speed. But often the "lightning speed" turns into lengthy projects,...

Security Robotics present themselves – System demonstration at the Continental Group
Lead companies in the technology sector always have their eyes and ears on the proverbial pulse of time. When groundbreaking technologies are presented at trade fairs and events, you can be sure to meet expert representatives of renowned companies and associations....

Integrative platform solutions as the core of any security concept
Again and again we speak of integrative security solutions, of networking, of the interaction of the most diverse security components. But what does this mean? What forms the basis for such an exchange to take place, for many things to become one big whole, which is...

Tariff increases as an opportunity for rethinking in the security industry
The United Services Workers' Union, or Ver.di for short, is a very strong and present trade union. Together with the BDSW, which has more than a quarter of a million members, the workers' representatives regularly campaign for wage adjustments and compensation for...

EU top politician Marion Walsmann visits Security Robotics
To help shape the digital future, you first have to understand it. And especially when it comes to topics such as AI, robotics and smart security systems, nothing is more enlightening than entering into an intensive discourse with inventors, innovators and precisely...

Why we should help shape the EU’s AI law.
Traditionally, the EU goes into the political summer break until the beginning of September. One topic that has occupied the representatives of the "Telecommunications Working Group" in particular right up to the last session is the so-called AI Act (Artificial...

Understanding and experiencing safety robots on the Innovation Days July 2022
"Today's innovation is tomorrow's standard." Especially in the field of robot systems and the associated hardware, sensors, software and network technology, this saying is 110% true. And so it is only logical to hold our Innovation Days several times a year. For...

Security robots and control centers, singleplayer or dreamteam?
"The whole is greater than the sum of its parts." Aristotle once said, summing up in one sentence what today would be simplified as "Together we are strong". For it is only through the interaction of different partners and the right selection of hardware and software...

Humans and robots – service partner for the future?
An ordinary morning in an ordinary company. An employee enters the main gate of the branch. His digital access authorisation is automatically recorded, verified and he can continue on his way without delay. Other employees approach with an unusual amount of luggage....

SPOT proves its skills at the DB Test Centre Delitzsch
The Security Robotics Innovation Days have become a permanent fixture in our own company and well-known companies also take part in the event every year full of curiosity. In September 2021, we got into conversation with Mr Schermann, CTO (Security) of Deutsche Bahn...

Security Robotics at the Dussmann Autonomous Day
Security Robotalk: State-of-the-art robot solutions for the modern facility management specialist Dussmann Service New technologies are conquering the world, gaining more and more importance in the course of digitalization - also in the facility management industry....

The start of something big: Security Robotics at the Munich SecurityExpo
Security Robotalk: AI and state-of-the-art robotics - Security Robotics comes to the Munich SecurityExpo The Munich Security Expo is known for its role as an innovator. What is shown here is the industry standard a few years later at the latest. For this reason, the...

The new precision work in security
Security Robotalk: Precision at the very highest level - this is how robots are used in industry There are industries that feel the technology shift more than others. One of these is the security industry. On the one hand, it feels it directly - through...

How safety robots change Industry 4.0
Security Robotalk: Guard, measure, accompany - this is how Industry 4.0 is changing the security industry with robots 3 am. Large pressure vessels stand on a huge factory site. Silence reigns. Only a light rhythmic and mechanical tapping can be heard. It is the...